Avast Firewall is another major component of Antivirus protection offered alongside Core Shields, and it is available for Windows workstations. Our Firewall monitors all network traffic between devices and the outside world to help protect you from unauthorized communication and intrusions.
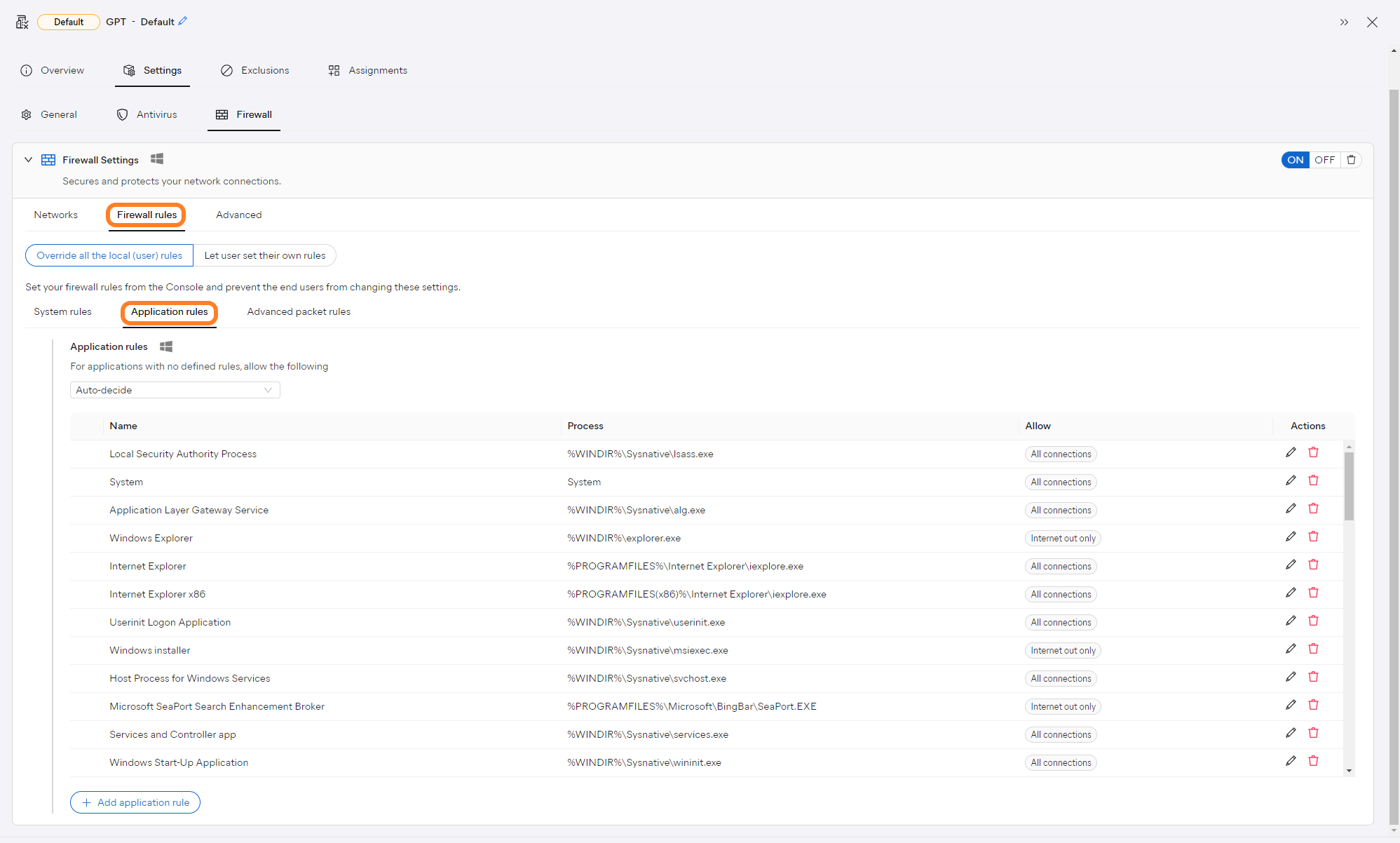
Firewall's application rules are specifically meant to control how Firewall behaves toward applications or processes when they connect to the internet or to another network. These rules are created each time an application or process makes a connection attempt for the first time. Advanced users can set connection permissions for each individual app to determine how strictly Firewall monitors any incoming or outgoing communication.
We recommend you only modify these rules if absolutely necessary. In most cases, Firewall formulates optimal rules without any user input.
To access Firewall application rules:
Although you can allow local configuration of all Firewall rules by selecting the Let user set their own rules option at the top of this section, we recommend choosing the Override all the local (user) rules option, ensuring these rules are controlled by your console for maximum security across your network.
Each policy contains default application rules to allow common applications to communicate properly. You can delete or modify these rules in order to change how the listed application communicates, or add new rules to the existing list.
You can also set the default action Firewall will take for new applications with no defined rules:
To add a new application rule:
The new rule will then be added to the list. You can edit/delete it if needed by clicking the pencil/trash bin icon in the Actions column. When modifying custom application rules, the options to add, edit, delete, or disable the packet rules will also be available.
Clicking Show system path variables in the Add Application Rule dialog will show all accepted system variables, and the tooltips will provide more information:
Use this if you need to specify an executable file located in a folder where shared program files for 32-bit applications are stored.
Example: %CommonProgramFiles(x86)%\app.exe → C:\Program Files (x86)\Common Files\app.exe
Use this if you need to specify an executable file located in a folder where program files for 32-bit applications are stored.
Example: %ProgramFiles(x86)%\app.exe → C:\Program Files (x86)\app.exe
Use this if you need to specify an executable file located in a folder where shared program files are stored.
Example: %CommonProgramFiles%\app.exe → C:\Program Files\Common Files\app.exe
Use this if you need to specify an executable file located in a folder where program files are stored.
Example: %ProgramFiles%\app.exe → C:\Program Files\app.exe
Use this if you need to specify an executable file located in a core folder of the operating system.
Example: %WINDIR%\SysNative\app.exe → C:\Windows\System32\app.exe
Use this if you need to specify an executable file located inside an operating system folder.
Example: %WINDIR%\app.exe → C:\Windows\app.exe
Use this if you need to specify an executable file located anywhere else on the system drive.
Example: %SYSTEMDRIVE%\folder_name\app.exe → C:\folder_name\app.exe
Clicking any listed variable will automatically add it to the Application Path field.
To customize an existing rule or create a new custom rule:
Other Articles In This Section: